The AI Revolution in Cybersecurity
In today's hyperconnected world, cyber threats loom larger than ever, posing existential risks to businesses of all sizes. The stakes are astronomically high: a single data breach can cost an Enterprise an average of $4.35 million
(IBM Cost of a Data Breach Report 2022), not to mention the irreparable damage to reputation and customer trust.
The imperative for medium and large enterprises is clear: traditional cybersecurity measures are no longer enough. So, how can this be tackled?
This blog explores the emerging role of AI in cybersecurity, providing valuable insights for businesses looking to enhance their security posture. We'll cover:
- Key concepts driving AI in cybersecurity
- Practical implementation strategies
- Challenges and solutions in AI adoption
- Real-world applications and success stories
- Steps to integrate AI into your security framework
Understanding AI in Cybersecurity: Key Concepts and Components
At the heart of AI-powered cybersecurity are four fundamental concepts that work in synergy to create robust defense systems:
- Artificial Intelligence and Machine Learning
AI simulates human intelligence processes, enabling systems to learn, reason, and self-correct. ML allows systems to improve their performance through experience.
69% of organizations report that ML significantly reduces the time to detect threats.
- Threat Detection and Automation
AI enhances threat detection by analyzing data from multiple sources in real-time. AI-driven automation performs routine tasks without human intervention.
According to the Accenture security report, Automation can reduce response times by up to 60%.
- Data Collection and Analysis
Effective AI-driven cybersecurity relies on processing vast amounts of data. AI models are trained on high-quality, diverse datasets.
Organizations using AI for data analysis report a 12% reduction in security breaches.
AI enhances threat intelligence by correlating data from multiple sources to provide a comprehensive view of the threat landscape. This enables organizations to anticipate & prepare for attacks rather than merely reacting.
78% of cybersecurity professionals state that threat intelligence is crucial for a strong security posture.
These concepts form the foundation of AI-powered cybersecurity, enabling more accurate, efficient, and proactive protection against evolving cyber threats.
The Dark Side: How Hackers Abuse AI
AI plays a significant role in bolstering cybersecurity measures, but it is essential to be aware of how cybercriminals leverage this technology to their advantage:
- Social Engineering Schemes: AI empowers cybercriminals to execute more advanced and tailored phishing attacks. By examining large amounts of data, AI can craft highly convincing messages that are more likely to deceive individuals or organizations.
- Password Hacking: With enhanced algorithms, cyber attackers can conduct quicker and more precise password-guessing attempts. AI algorithms can swiftly crack passwords by analyzing patterns and common combinations, posing a heightened risk to digital security.
- Deepfakes: The advent of AI-generated audio and video content has given rise to deepfake technology, enabling cybercriminals to create realistic impersonations for fraudulent activities. Deepfakes can be used for identity theft, spreading misinformation, or manipulating individuals into disclosing sensitive information.
- Data Poisoning: Hackers manipulate training data used by AI systems to influence algorithmic decisions in a practice known as data poisoning. By injecting malicious data into the training process, cybercriminals can compromise the integrity and reliability of AI-powered security defenses.
Understanding these tactics employed by cybercriminals is crucial for developing robust cybersecurity strategies that can effectively mitigate evolving threats in the digital landscape. Organizations must stay vigilant and implement comprehensive security measures to safeguard against sophisticated AI-driven cyber attacks.
How Can You Strengthen Your Business With AI in Cybersecurity?
As technology advances, the importance of cybersecurity for businesses cannot be overstated. With the advancement of artificial intelligence in cybersecurity, businesses have a powerful tool to enhance their digital security measures.
But how exactly can your business leverage AI to solidify its cybersecurity defenses? Let's explore the various ways AI is revolutionizing the cybersecurity landscape.
Implementing AI in Your Cybersecurity Strategy: Best Practices
In a recent survey in April 2024 by Gartner, 75% of organizations plan to operationalize AI for cybersecurity by 2025. To effectively integrate AI into your cybersecurity framework, consider the following best practices:
- Developing Robust AI Models
- Use high-quality, diverse datasets for training
- Continuously evaluate and update models
- Seamlessly integrate AI models with existing security infrastructure
- Leveraging Automation
- Implement automated systems for real-time threat monitoring
- Develop automated response protocols for swift threat mitigation
- Utilize continuous monitoring to assess the security landscape
- Enhancing Threat Intelligence
- Correlate data from multiple sources using AI
- Implement predictive analytics to anticipate potential threats
- Cooperate with other organizations to share threat intelligence
Overcoming Challenges in AI-Powered Cybersecurity
While AI offers tremendous benefits, it also presents unique challenges:
- Data Quality
- Challenge: Ensuring the accuracy and relevance of data used to train AI models.
- Solution: Implement rigorous data validation processes and regularly update training datasets.
- Outcome: Reduction in errors by up to 30%
- Minimizing False Positives
- Challenge: Reducing the number of false alarms generated by AI systems.
- Solution: Continuously tune AI models and incorporate human oversight to improve accuracy.
- Outcome: Can reduce false positives by 50%
- Adapting to Evolving Threats
- Challenge: Ensuring AI systems can respond to new and evolving threats.
- Solution: Develop AI systems with adaptive learning capabilities and regularly update threat databases.
- Outcome: Improves threat detection by 35%
Managing these challenges requires a multi-faceted approach, combining technological solutions with organizational policies and human expertise. By doing so, brands can maximize the benefits of AI in cybersecurity while minimizing potential drawbacks.
Key Principles for Effective AI Integration into Your Enterprise
A study by MIT Sloan Management Review discovered that businesses that effectively integrate AI into their operations are five times more likely to be high performers. To maximize the benefits of AI in your cybersecurity strategy, adhere to these five key principles:
- Layered Security: Implement a multi-layered approach that combines AI with traditional security measures.
This "defense in depth" strategy can reduce the risk of successful attacks by up to 70%.
- Proactive Defense: Use AI's predictive capabilities to prevent threats before they materialize.
Compared to reactive approaches, proactive measures can reduce security incidents by up to 50%.
- Continuous Improvement: Regularly update and refine AI models based on new data and emerging threats.
|
Pro tip: Aim for monthly model updates to maintain a 95% or higher threat detection accuracy.
|
- Transparency and Explainability: Ensure AI decision-making processes are transparent and explainable. This will build trust and help comply with regulations like GDPR.
- Human-AI Collaboration: Foster a symbiotic relationship between human experts and AI systems.
Studies show that this collaboration can improve threat detection accuracy by up to 30% compared to AI or human analysis alone.
These principles can help organizations create a robust, adaptive, and effective AI-powered cybersecurity framework that evolves with the threat landscape.
AI in Action: Real-World Applications and Trends
Integrating AI for cybersecurity is not just theoretical; it significantly impacts real-world scenarios. Here are some compelling examples:
- Network Security: AI-powered systems monitor network traffic in real-time, identifying anomalies that might indicate a cyber attack.
For instance, Darktrace's Enterprise Immune System uses AI to create a 'pattern of life' for every user and device on a network. Any deviation from this pattern triggers an alert, allowing for rapid response to potential threats.
- Endpoint Protection: AI is revolutionizing endpoint security by providing more sophisticated threat detection and response capabilities.
CrowdStrike's Falcon platform uses AI to analyze endpoint activity and automatically detect and prevent advanced threats, significantly reducing the time to notice and respond to incidents.
- Phishing Detection: AI algorithms detect and filter out phishing emails more accurately than traditional rule-based systems.
Google's Gmail uses machine learning models to block over 100 million phishing attempts daily, demonstrating AI's power in combating one of the most common cyber threats.
- Vulnerability Management: AI is helping organizations prioritize and manage vulnerabilities more effectively.
Kenna Security uses machine learning to analyze threat data and predict which vulnerabilities will most likely be exploited. This allows security teams to concentrate their efforts where they're most needed.
- Behavioral Analytics: AI-powered behavioral analytics are being used to detect insider threats and compromised accounts.
Exabeam's Security Management Platform uses machine learning to establish baselines of normal user behavior and flag anomalies that could indicate a security breach.
Top 10 Developments in AI Cybersecurity
The field of AI in cybersecurity is rapidly evolving. Here are some of the latest advancements:
- AI-Powered Remediation: Tools like Secureframe Comply offer automated remediation capabilities, providing step-by-step instructions to address security issues. This speeds up the resolution process and helps maintain continuous compliance.
- Enhanced Threat Intelligence: Google's Cloud Security AI Workbench uses specialized AI models to analyze and summarize security threats, improving detection accuracy by up to 40%. This allows security teams to understand and respond to complex threats quickly.
- Security Questionnaire Automation: AI is streamlining vendor risk assessments by automating the process of answering security questionnaires. This technology can suggest answers based on existing data and policies, significantly reducing the time and effort required for vendor assessments.
- Dynamic Deception Capabilities: Platforms like Acalvio's ShadowPlex use AI to create realistic decoys that trap and analyze attacker behavior. This provides valuable insights into attacker tactics and helps in proactive threat mitigation.
- AI-Assisted Secure Development: Tools like GitHub Copilot are helping developers write more secure code by suggesting secure coding patterns and identifying potential vulnerabilities during the development process.
- Automated Penetration Testing: AI-powered tools are automating various aspects of penetration testing, enhancing the efficiency and coverage of security assessments. These tools can identify vulnerabilities and suggest exploitation methods, mimicking real-world attackers.
- AI-Based Patch Management: AI systems prioritize patching, ensuring that the most critical vulnerabilities are addressed first. This helps organizations manage the overwhelming volume of security updates more effectively.
- Quantum-Resistant Cryptography: With the looming threat of quantum computing, AI is being used to develop and test quantum-resistant encryption algorithms, ensuring data security in the post-quantum era.
- AI-Driven Security Orchestration: Advanced Security Orchestration, Automation, and Response (SOAR) platforms leverage AI to automate and orchestrate complex security workflows, significantly improving incident response times.
- Explainable AI in Cybersecurity: There's a growing focus on developing AI models to explain their decision-making process. This "explainable AI" is crucial for building trust in AI-driven security decisions and complying with regulatory requirements.
These developments showcase the ongoing evolution of AI in cybersecurity, promising even more advanced and effective security solutions shortly.
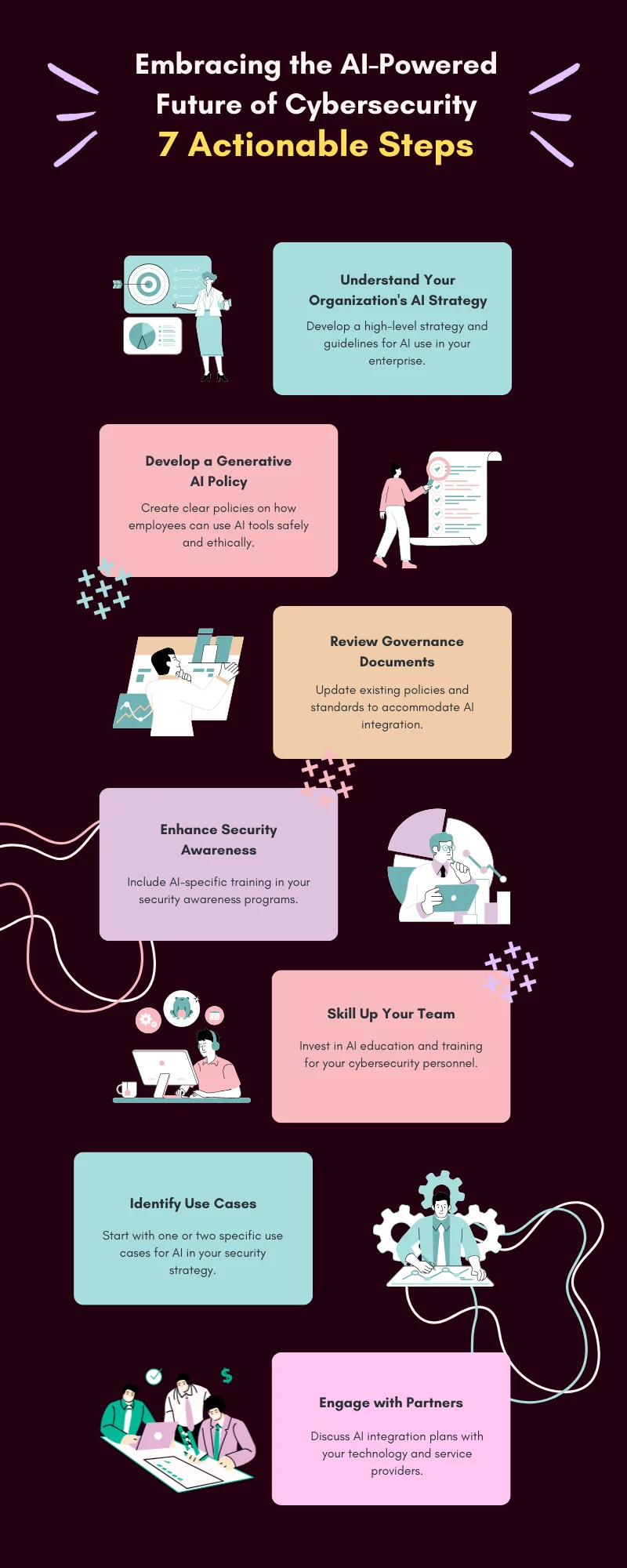
Implementing AI in Your Enterprise: 7 Actionable Steps
A report by Accenture found that 74% of organizations struggle to scale their AI implementations.
To ensure the successful integration of AI for your cybersecurity efforts, follow these seven actionable steps:
-
Develop a Comprehensive AI Strategy
-
Assess your cybersecurity posture, identifying gaps where AI can impact most.
-
Set clear goals and KPIs for AI integration, aiming for at least a 30% improvement in key metrics.
-
Align AI strategy with overall business objectives to ensure executive buy-in.
-
Create Clear AI Usage Policies
-
Define guidelines for ethical AI use, ensuring compliance with regulations like GDPR.
-
Establish protocols for data handling and privacy, with a goal of 100% compliance.
-
Implement a governance framework for AI decision-making processes.
-
Update Governance Frameworks
-
Revise existing policies to accommodate AI, covering all aspects of AI use in cybersecurity.
-
Implement new AI-specific governance measures, including regular audits of AI systems.
-
Establish oversight committees for AI initiatives, including IT, legal, and business unit representatives.
-
Enhance AI-Focused Security Training
-
Develop AI-specific modules for security awareness programs, aiming for 100% employee completion.
-
Train IT staff on AI cybersecurity tools and techniques to certify 80% of relevant staff.
-
Educate leadership on AI benefits and risks to ensure informed decision-making.
- Invest in AI Skill Development
- Identify skills gaps in your cybersecurity team through comprehensive assessments.
- Provide AI and ML certification opportunities, aiming to upskill 50% of your team within a year.
- Consider partnering with academic institutions for talent development and research collaboration.
- Identify Specific AI Use Cases
- Start with 1-2 pilot projects in high-impact areas, such as threat detection or incident response.
- Observe and measure the effectiveness of AI implementation, aiming for a 25% improvement in target metrics.
- Scale successful use cases across the organization to implement AI in 80% of security operations within two years.
- Collaborate with AI-Savvy Partners
- Start with 1-2 pilot projects in high-impact areas, such as threat detection or incident response.
- Monitor & measure the effectiveness of AI implementation, aiming for a 25% improvement in target metrics.
|
Pro tip: Scale successful use cases across the organization to implement AI in 80% of security operations within two years.
|
Conclusion
As cyber threats continue to evolve, with global cybercrime costs projected to reach $10.5 trillion yearly by 2025, integrating AI and ML in cybersecurity is no longer optional—it's imperative. By embracing AI for cybersecurity, businesses can significantly enhance their ability to notice, prevent, and respond to cyber threats.
However, successful implementation requires a strategic approach, continuous learning, and a balance between AI capabilities and human expertise.
Take the first step towards AI in cybersecurity today. Assess your security posture, identify key areas for AI integration, and start your journey toward a more secure digital future.
However, you also want to make your brand stand out globally. In that case, our team of experienced SEO website content writers and SEO specialists is committed to helping boost your visibility and hook you with your target audience. For more solutions, Visit us at LexiConn or email us at [email protected].
Boost your Content Strategy.
Download the Free eBook now.
Unlock Generative AI's potential for content marketing success. Unearth its impact on teams and businesses. Witness real-life examples and case studies, showcasing AI-driven content ingenuity.